Enterprises
Various large corporations globally have lot of employees who work on Enterprise Apps from their mobile devices, whether corporate given or embracing Bring Your Own Device (BYOD) where devices are personal devices but still running corporate Apps or Email on them.
Most of big enterprises have deployed a Mobile device Management solution like Airwatch, Mobileiron, Microsoft Intunes, Soti, IBM Maas360 etc but still struggle to get enterprise visibility on next generation threats coming from various Device , Network , Applications & Phishing based threats which is applicable today.
Zimperium is unique & Enterprise choose us because of the following:
Mobile Security that Uses Machine Learning to Detect Cyber Attacks
Next-Generation, On-Device Mobile Device
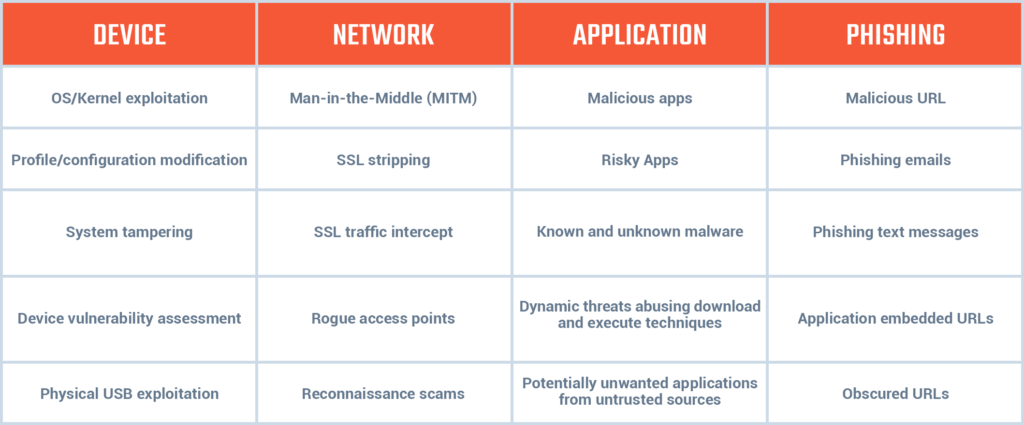
z9™ is the revolutionary Mobile Threat Defense engine developed by our team of advanced mobile security researchers and developers at Zimperium. z9™ uses machine learning to detect device, network, phishing and application mobile attacks on-device and in real time. The z9™ engine was specifically developed for mobile, not ported from traditional endpoint security, to guard against the unique threats targeting iOS , Android and Chromebook devices. z9™ runs efficiently on-device, without introducing latency or violating user privacy.


Like A Central Nervous System For Your Mobile Device
Much like your nervous system continuously monitors your body from the inside, z9™ can detect both known and unknown threats by analyzing the behavior of a mobile device. By analyzing slight deviations to the mobile device’s OS statistics, memory, CPU and other system parameters, z9™ can accurately identify not only the specific type of malicious attack, but also provide forensics associated with the who, what, where, when and how of an attack occurrence.
Stop Zero-Day Threats Without Signatures Or Lookups
Unlike other threat detection systems, z9™ monitors the entire mobile device for malicious behavior regardless of the attack entry point. The device-wide resident approach does not rely on external IDs or malware signatures, and does much more than app scanning. This makes z9™ immune to evasion techniques such as polymorphic malware, virtual machine awareness, download and execute techniques or binary obfuscation, allowing Zimperium solutions to find and protect against both known, zero-day or new threats even when disconnected from the network.
Solution By Industry
- Government
- Forensics
- Financial Services
- Enterprise
Quick Links
- Why Cyber Armor
- Partners
- Jobs
- Contact
Contact Us
- City Tower, Sheikh Zayed Road, Dubai.
- : +91 8899348143
- +91 9717876547
- contact@cyberarmors.com

